Detect and Respond to cyber threats faster with our Autonomous End-point Breach Protection.
Let our team monitor and detect cybersecurity threats against your network, users, files and hosts 24/7 via our ThreatFortress Cynet360 XDR and Response Automation platform.

Automated Response Remediation End-point Monitoring
Real-time Detection and
Response to Cyber Threats

Cyber Alert Monitoring

Threat Hunting

Cyber Attack Investigation
Protecting companies from 5 devices to 10,000 around the world.





Review the demo of the Sterling 360 Cybersuite (powered by Cynet Fusion Sensor) and how it can help protect your business. Let us prove the value of our Sterling 360 Cybersuite or 30 days at no cost!
Experienced a breach and need live response? Please use the live chat or Call: +1 (888) 302.5524 or Email: cyberteam@sterlinginfo.com Our team can help you remediate your breach and protect your systems within hours.
Sterling 360 Cybersuite Features

24/7 Availability
Ongoing operations at all times, both proactively and on-demand per the customer’s specific needs.

Exclusions, Whitelisting and Tunnelling
Adjusting our alerting mechanisms to the customers’ IT environment to reduce false positives and increase accuracy.

On Demand Analysis
Customers can send suspicious files to analysis directly from the console and get an immediate verdict.

Remediation Instructions
Conclusion of investigated attacks entails concrete guidance to the customers on which endpoints, files, user and network traffic should be remediated.

Alert Monitoring
Continuous management of incoming alerts: classify, prioritize and contact the customer upon validation of active threat.

Threat Hunting
Proactive search for hidden threats leveraging our SOC investigation tools and over 30 threat intelligence feeds.

Attack Investigation
Deep-dive into validated attack bits and bytes to gain the full understanding of scope and impact, providing the customer with updated IoCs.

We Are One Click Away
CISOs can engage CyberOps with a single click on the Dashboard App upon suspicion of an active breach.
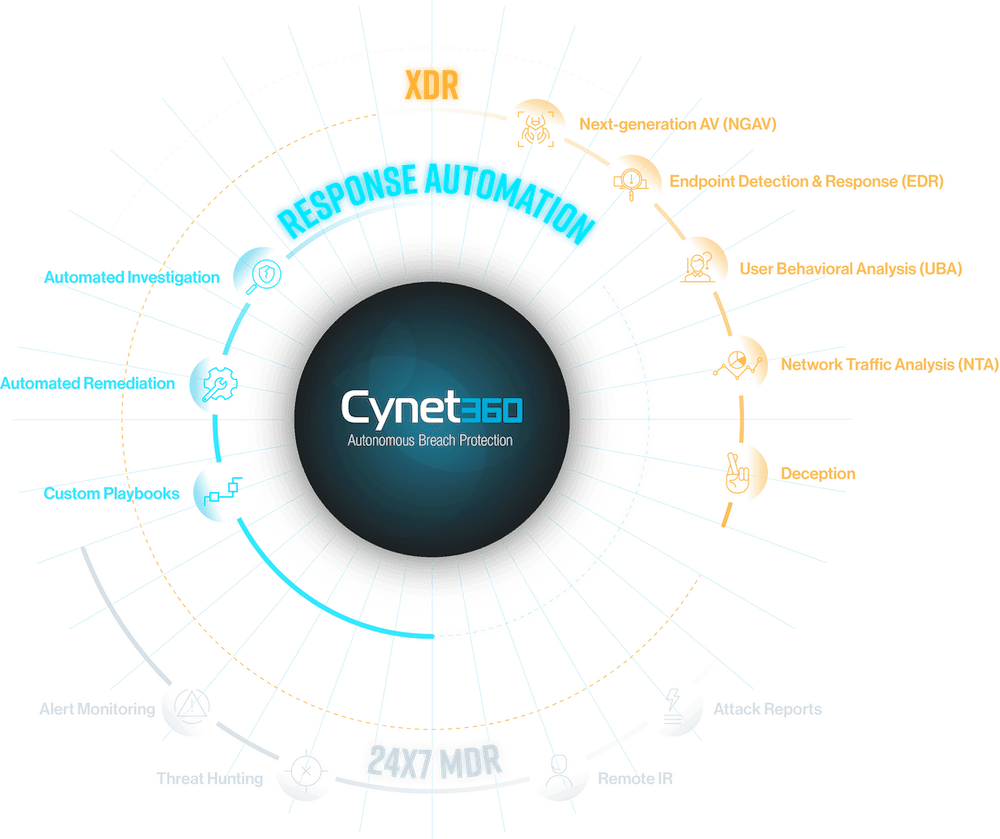
AUTONOMOUS BREACH PROTECTION
Our XDR prevents and detects threats on endpoints, networks, and users and triggers for each identified threat an automated investigation flow that reveals the attack’s scope and root cause and applies automated remediation. The 24×7 SOC team continuously monitor and optimize this process to maintain top quality and precision
Learn more
Deception Technology Included
The Deception technology plants various types of decoys across the environment to tempt attackers to get out of their hidings and reach out for what seems to be a valuable hunt and by doing that reveal their presence and former activities. With Cynet Deception technology there are zero false positives – only live malicious presence can trigger a deception alert.
Learn more
Secure Connectivity.
Maximum Productivity.
Your workforce needs seamless connection to their environments, you need security.
With Cyolo Zero Trust Access, it’s easy to keep users securely connected – whomever they are, wherever they are.

How Cyolo Keeps Your Business Connected & Secure
Connecting any User to any System,
on any Network and Platform

Resilient
- Enforce granular & action based policy
- Minimize the attack surface with no access to the network
- Reduce risk of internal and external threats with risk-based access
Agile
- Network and platform agnostic – on premise, IaaS and SaaS platforms
- Remove the need to connect to users’ networks, NACs etc.
- Easily expand to new locations with no infrastructure or hardware required

Boundless
- Unified secure access to applications on any network: internal, external, offline and IoT
- Deliver a secure and transparent user experience
- Get self-calibrating actionable insights
Customer Quotes
Secure Access to Support Your Business

Controlled Access
>>
Full visibility and control over access and actions in sensitive applications & mission-critical environments. Providing controlled access for DevOps, developers and privileged users, Cyolo is expert in privileged access management.

Compliance Readiness
>>
Ensure your users’ traffic and information is never exposed.
Obtain compliance with legacy applications and systems through encrypted traffic, MFA & biometric authentication.

Secure Remote Access
>>
Connect remote users to applications, desktops, servers and files - VPN and network free.
Supervised access and actions for sensitive roles and areas, Cyolo provides one of the best VPN alternatives.

Third Party Collaboration & M&A
>>
Facilitate cross organizational connectivity by securely connecting users to shared applications.
No network integration or trust relationship between users’ directories required

Risk Base Access
>>
Get AI powered policy suggestions and self-calibrating actionable insights.
Visualize risk profiles and set a risk-based policy


